The recent COVID-19 pandemic has forced many businesses, agencies, and individuals to adopt digital services for communication, work production, and collaboration. Digital transformation of workflows, communication, financial transactions, and so on was expected, but due to the pandemic, the change occurred unexpectedly very fast.
Many have experienced a lack of preparedness for such a digital transformation. Due to such a surge in digital services, cybersecurity attackers and scammers are leaving no stones unturned to capitalize on vulnerabilities of digital services.
Cybersecurity has become the most critical challenge in the present context, with many works shifting to digital platforms.
The digital transformation has become an urgency to maintain social distancing and, at the same time, keep the work going. Social Distancing and Work from Home have become the new normal.
However, the rush to produce work has opened windows for attackers, compromising the privacy of many.
The primary reason behind this is the lack of digital literacy and preparedness as well as cybersecurity awareness at the individual level and cybersecurity preparedness at the organizational level.
In this article, we will review some of the most common cybersecurity attacks reported during the pandemic and provide recommendations to protect from such attacks.
During the pandemic, every country has published reports of at least one or two cases of COVID-19 themed cyberattacks. Let's look at some threats that we are exposed to in the wake of the pandemic.
Since employees are working from home, phishing has become a go-to attack for threat actors.
This type of attack tricks email or SMS recipients into believing that the email/SMS is from a reliable source.
These emails can be disguised as health advice from WHO and UNICEF.
When users open such messages, it can either compromise users'' sensitive data by asking to fill a form or install malicious applications on their device.
The worst part is that this all happens without the user's knowledge or consent.
The trend of attacking devices through malware hidden in mobile apps has increased recently.
The app developers use coronavirus-related keywords to bring these apps to the top search results in app stores.
According to a report from CheckPoint Research, 16 such apps that claimed to offer information on the virus outbreak, contained malware.
Online shopping has also surged during the pandemic, and who doesn't love to get discounts while shopping online?
While most online shopping platforms are malware-proof, attackers are exploiting this opportunity by promoting tools on the darknet with ''COVID19'' or ''coronavirus'' as discount codes.
Some hackers were advertising the sales of sanitizers, face masks, and PPE kits online. It was part of a desperate attempt to launder cash from email scams.
In Europe, the pharmaceutical company got away with €6.64 million, and the buyers never received their deliveries.
Every individual's data is a gold mine for attackers and data brokers.
There are cases of hospital record system breach where attackers got access to vital information of patients.
By holding such digital information hostage, cybercriminals ask for ransom in exchange for not releasing the data.
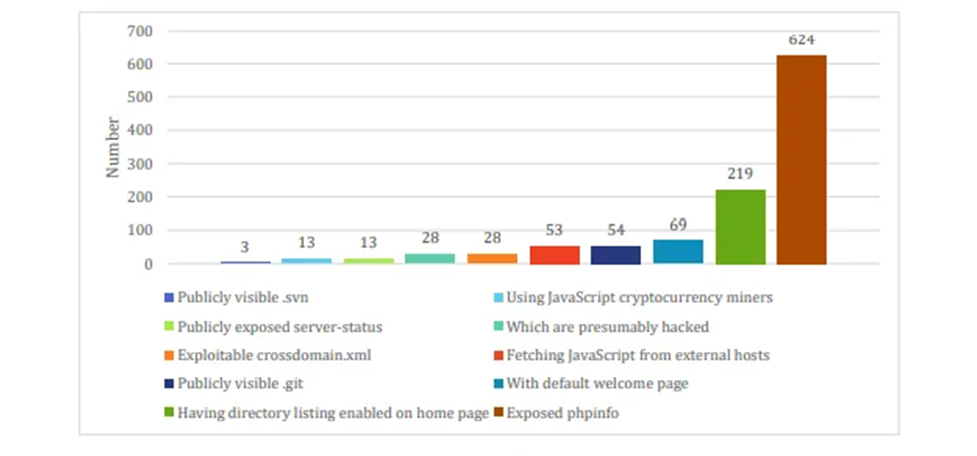
According to a survey from 2017, a total of 756 ".np" websites were defaced. Out of these sites, 332 were commercial websites (.com.np) and 160 were government websites (.gov.np).
The first step on the to-do-list to prevent cyberattacks should be assessing the vulnerabilities of digital platforms. It's better to understand first-hand that software or applications are never risk-free.
Most of the version updates and patches should include a security assessment and fix. The more people use applications, the more issues are identified.
Therefore, testing and maintenance of digital platforms shall never be stopped.
Organizations need to have the capability to eliminate vulnerabilities immediately after their discovery.
Moreover, users and organizations also need to assess if the applications are being used wrong. There may be a more secure way to use them, which is usually valid for most applications that offer premium versions.
The premium versions are always more secure, but again, most users would prefer the free versions of software and digital platforms. An individual's choice of using a free version of a software/tool may not necessarily meet the security requirements of an organization.
Individuals and organizations that are not able to assess risks of cybersecurity attacks may follow best practices and take expert advice in protecting themselves from cybersecurity attacks.
Critical systems or applications such as Virtual Private Networks (VPNs), cloud interfaces, firewalls, meeting tools, collaboration systems, and email servers need constant updates. This can help eliminate vulnerabilities soon after their discovery.
Most users tend to use passwords that are easier to remember, and in doing so, they don't realize that it makes attackers easy to guess the passwords.
Therefore, the use of complex passwords reduces the risk of unauthorized access attacks.
Also, employees working remotely need to use multifactor authentication (MFA) to access network connections and critical applications.
Mixing personal and professional aspects have never been appropriate - either it's's in life in general or at work.
Saving office work on personal storage or cloud is not a good idea. Users need to establish good cyber hygiene to use official email accounts or cloud storage to store official work.
It prevents the risk of information leak if one of the personal or work services gets compromised, another can remain protected.
There are a few digital platforms that support extensive remote work, while others lack the basic features and security.
For example, an employee without prior experience in extensive remote work using VPN may find it difficult even to set up a client VPN in their devices.
Therefore, it would be better to provide support to the employees in setting up minimum security requirements such as MFA and VPN on their devices.
Similarly, the use of verified tools and services from trusted vendors will have a lesser risk of data breach and cyberattacks.
In phishing scams, the attacker poses as someone or something to steal credentials. This can happen while opening an attachment or clicking a malicious link in an email.
It is of utmost importance for the users to understand and identify such threats.
90% of ransomware attacks originate from phishing attempts.
Therefore, here are some tips to follow to protect from such scams or threats.
● Avoid opening emails from people you don't know or from senders that seem suspicious in any way.
● Know which links are safe to click and which are not. To do so, hover over the link to know where it redirects to.
● There's a high chance that malicious links or attachments may come from friends whose mail may have been compromised as well. Therefore, make sure to verify if you were not expecting such emails.
● Pay a closer look at the email details. Make sure to check grammatical errors, senders detail, and subject.
Everybody loves free services. Public WiFi, although open, poses a higher level of security risk. Working from home over the public WiFi should be prohibited.
Public WiFi should be the last resort but is not recommended if users don't have a client VPN setup.
Enabling VPN ensures an encrypted connection between the user's device and the server making it difficult for cybercriminals to access the transmitted data.
Similarly, mobile networks can also be used if client VPN is unavailable.
It is a top priority to safeguard online accounts and monitor them. Employees'', customers'', and users'' online accounts may be compromised, and sensitive data such as personal details, credit/debit card information, and health information get leaked.
Such a breach of privacy may happen at any time. Therefore, it's better to monitor for suspicious activities and unauthorized access regularly.
Reminding employees, customers, and users about their role in keeping a secure password, using MFA, updating PINs, etc. would help reduce data breach due to cybersecurity attacks.
COVID-19 pandemic has allowed innovative ways of working from home and is bringing digital transformations in many organizations.
However, for attackers, it has created opportunities for security and privacy breach.
Organizations that use digital platforms need to be aware of the risks of adopting digital platforms beforehand, build cybersecurity preparedness, and monitor the platforms for any suspicious activities to provide a safe and secure digital online experience to employees, customers, and users.
Image Source: Source: Threat Report 2017 Nepal From ThreatNix